

March 16, 2021

Data security is the process of protecting #digital data. It is the protection of files, databases, and accounts on a network. Digital data needs protection from destructive forces and unwanted actions of unauthorised users, like a cyberattack or a data breach. This is done using collective controls, applications, and techniques that identify the relative importance of various datasets, their sensitivity,
and regulatory compliance requirements. Then appropriate protections are applied to secure those resources.
Data security isn’t the be all and end all of security practice. It is one method of evaluating and reducing the danger that comes with storing any type of data. The core elements of knowledge security are:
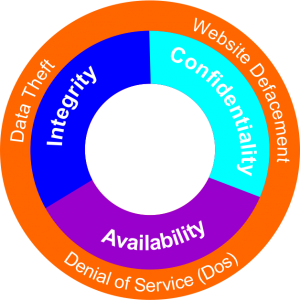
This is also commonly called the #CIA triad. It is the security model and guide for organisations to keep their sensitive data shielded from unauthorised access and #data exfiltration. Data exfiltration is a form of security breach when data is copied, transferred, or retrieved from a computer or server without authorisation.
The first and most important question you should ask your #software solution provider is where and how your data is stored. It is always important to know what your solution provider does with your information. You should take a full run-down of safety protocols, procedures and take an explanation of how all of those assets are protected. It will fare you well to be proactive and understand how your information is safeguarded.
Data security includes encryption, hashing, tokenisation, and key management practices that protect data across all applications and platforms. The following data security technologies prevent breaches, reduce risk and sustain protections.
Data auditing is essential for an organisation to test and assess the overall security including cybersecurity. If and when a security breach takes place, having a data auditing solution in place helps capture and report on access control changes to data, who had access to sensitive data, when it had been accessed, file path, etc. If #data auditing is in place, it gives IT administrators the visibility necessary to stop unauthorised changes and potential breaches.
By monitoring data activity and suspicious behavior in real-time, it will be easier to quickly discover security breaches that cause accidental destruction, loss, alteration,
Data risk assessments helps you to identify overexposed sensitive data. #Risk assessment will also identify reliable and repeatable steps to prioritise and fix serious security risks. The process involves identifying sensitive data accessed via global groups, stale data, and inconsistent permissions. Risk assessments expose data vulnerabilities and provide an in-depth analysis of every vulnerability.
The last decade of IT management has seen a significant rise in the perception of data. Previously, having more data was considered better than less. However today, data is a liability. The threat of a data breach, incurring financial loss or stringent regulatory laws reinforce the thought that possessing data beyond the necessary amount can be extremely dangerous.
Data that is not on your network is data that cannot be compromised. Install systems to track file access and automatically archive unused files. Set a process to identify forgotten servers that are no longer in use.
A common data management error is placing a sensitive file on a platform open to the entire organisation. Get better control of your data with a data security software that is constantly able to classify sensitive data and keep it in a secure location.
In a technology driven world, there are regulations in place which require that organisations:
In a technology driven world, there are regulations in place which require that organisations:
Enter your details & we’ll be get in touch to discuss your project.
1800 11 6474
info@cipl.org.in
© 2022 Corporate Infotech Pvt. Ltd. All Rights Reserved.
Design by RAJMITH